What is a Honeypot
A honeypot is a security mechanism that creates a virtual trap to lure attackers. An intentionally compromised computer system allows attackers to exploit vulnerabilities so you can study them to improve your security policies. You can apply a honeypot to any computing resource from software and networks to file servers and routers.
Honeypots are a type of deception technology that allows you to understand attacker behavior patterns. Security teams can use honeypots to investigate cybersecurity breaches to collect intel on how cybercriminals operate. They also reduce the risk of false positives, when compared to traditional cybersecurity measures, because they are unlikely to attract legitimate activity.
Honeypots vary based on design and deployment models, but they are all decoys intended to look like legitimate, vulnerable systems to attract cybercriminals.
Production vs. Research Honeypots
There are two primary types of honeypot designs:
- Production honeypots—serve as decoy systems inside fully operating networks and servers, often as part of an intrusion detection system (IDS). They deflect criminal attention from the real system while analyzing malicious activity to help mitigate vulnerabilities.
- Research honeypots—used for educational purposes and security enhancement. They contain trackable data that you can trace when stolen to analyze the attack.
Types of Honeypot Deployments
There are three types of honeypot deployments that permit threat actors to perform different levels of malicious activity:
- Pure honeypots—complete production systems that monitor attacks through bug taps on the link that connects the honeypot to the network. They are unsophisticated.
- Low-interaction honeypots—imitate services and systems that frequently attract criminal attention. They offer a method for collecting data from blind attacks such as botnets and worms malware.
- High-interaction honeypots—complex setups that behave like real production infrastructure. They don’t restrict the level of activity of a cybercriminal, providing extensive cybersecurity insights. However, they are higher-maintenance and require expertise and the use of additional technologies like virtual machines to ensure attackers cannot access the real system.
Honeypot Limitations
Honeypot security has its limitations as the honeypot cannot detect security breaches in legitimate systems, and it does not always identify the attacker. There is also a risk that, having successfully exploited the honeypot, an attacker can move laterally to infiltrate the real production network. To prevent this, you need to ensure that the honeypot is adequately isolated.
To help scale your security operations, you can combine honeypots with other techniques. For example, the canary trap strategy helps find information leaks by selectively sharing different versions of sensitive information with suspected moles or whistleblowers.
Honeynet: A Network of Honeypots
A honeynet is a decoy network that contains one or more honeypots. It looks like a real network and contains multiple systems but is hosted on one or only a few servers, each representing one environment. For example, a Windows honeypot machine, a Mac honeypot machine and a Linux honeypot machine.
A “honeywall” monitors the traffic going in and out of the network and directs it to the honeypot instances. You can inject vulnerabilities into a honeynet to make it easy for an attacker to access the trap.
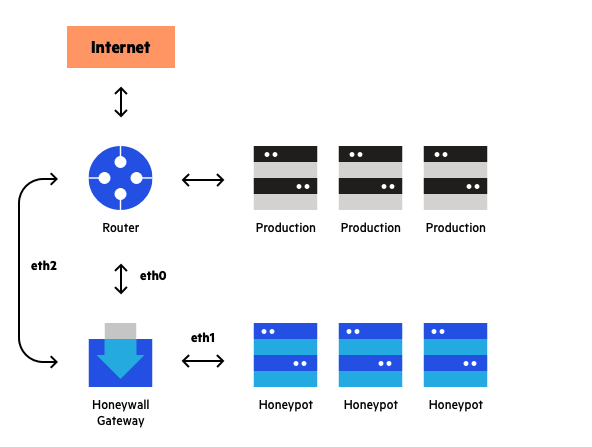
Example of a honeynet topology
Any system on the honeynet may serve as a point of entry for attackers. The honeynet gathers intelligence on the attackers and diverts them from the real network. The advantage of a honeynet over a simple honeypot is that it feels more like a real network, and has a larger catchment area.
This makes honeynet a better solution for large, complex networks – it presents attackers with an alternative corporate network which can represent an attractive alternative to the real one.
Spam Trap: An Email Honeypot
Spam traps are fraud management tools that help Internet Service Providers (ISPs) identify and block spammers. They help make your inbox safer by blocking vulnerabilities. A spam trap is a fake email address used to bait spammers. Legitimate mail is unlikely to be sent to a fake address, so when an email is received, it is most likely spam.
Types of spam traps include:
- Username typos—the spam filter detects typos resulting from human or machine error, including and sends the email into the spam folder. This includes misspelled email addresses like, for example, jhon@labra.com instead of the real john@labrat.com.
- Expired email accounts—some providers use abandoned email accounts or expired domain names as spam traps.
- Purchased email lists—these often contain many invalid email addresses that can trigger a spam trap. Additionally, since the sender didn’t gain authorization to send emails to the accounts on the list, they can be treated as spammers and blacklisted.
Spam trap vulnerabilities include generating backscatter (incorrectly automated bounce messages) and tainting legitimate email addresses that reply to or forward the message.
Moreover, once the spam trap has been exposed, it spammers can exploit it by sending legitimate content to it, causing the spam trap to lose its efficacy. Another risk is that some people may write to an address without realizing that it is a spam trap.
Accidentally hitting a spam trap can damage your organization by affecting your reputation and deliverability. An ISP might block or blacklist your IP address and companies that consult anti-spam databases will filter your emails.
Imperva Application Security
Our internal security team maintains the Imperva application security stack and conducts research on new and growing threats. The security team maintains your WAF, continuously updates security policies, identifies new vulnerabilities and threats, and creates custom rules according to your needs.
Instead of using traditional honeypots we leverage learning and findings from attacks seen across hundreds of thousands of Imperva protected domains, to deepen our understanding of threats in the wild. This research informs our multi-layered protection solution.
Imperva’s multi-layered protection for websites and applications ensures availability, security, and usability.
Imperva application security solutions include cloud and gateway web application firewalls (WAFs), a developer-friendly content distribution network (CDN) for improved performance, protection against distributed denial of service (DDoS) attacks, attack analytics to respond to actual security threats, and more.














