
Millions of mail servers running vulnerable Exim mail transfer agent (MTA) versions are currently under siege, with attackers gaining permanent root access via SSH to the exploited machines according to security researchers.
The flaw tracked as CVE-2019-10149 and named "The Return of the WIZard" by Qualys, the research outfit which discovered it, makes it possible for attackers to remotely run arbitrary commands as root — in most cases — on exposed servers after exploitation.
When we first reported about the critical severity vulnerability found in Exim versions 4.87 to 4.91, a quick Shodan search showed that vulnerable versions of Exim were running on more than 4,800,000 machines, with roughly 588,000 servers having already installed the patched Exim 4.92 release.
Now, Shodan says that over 3,680,000 servers are running a vulnerable version of Exim, while the number of patched machines has increased to 1,765,293.

Furthermore, as RiskIQ Leading Threat Researcher Yonathan Klijnsma detailed on Twitter, "people have been actively patching Exim servers the day the CVE-2019-10149 was published."
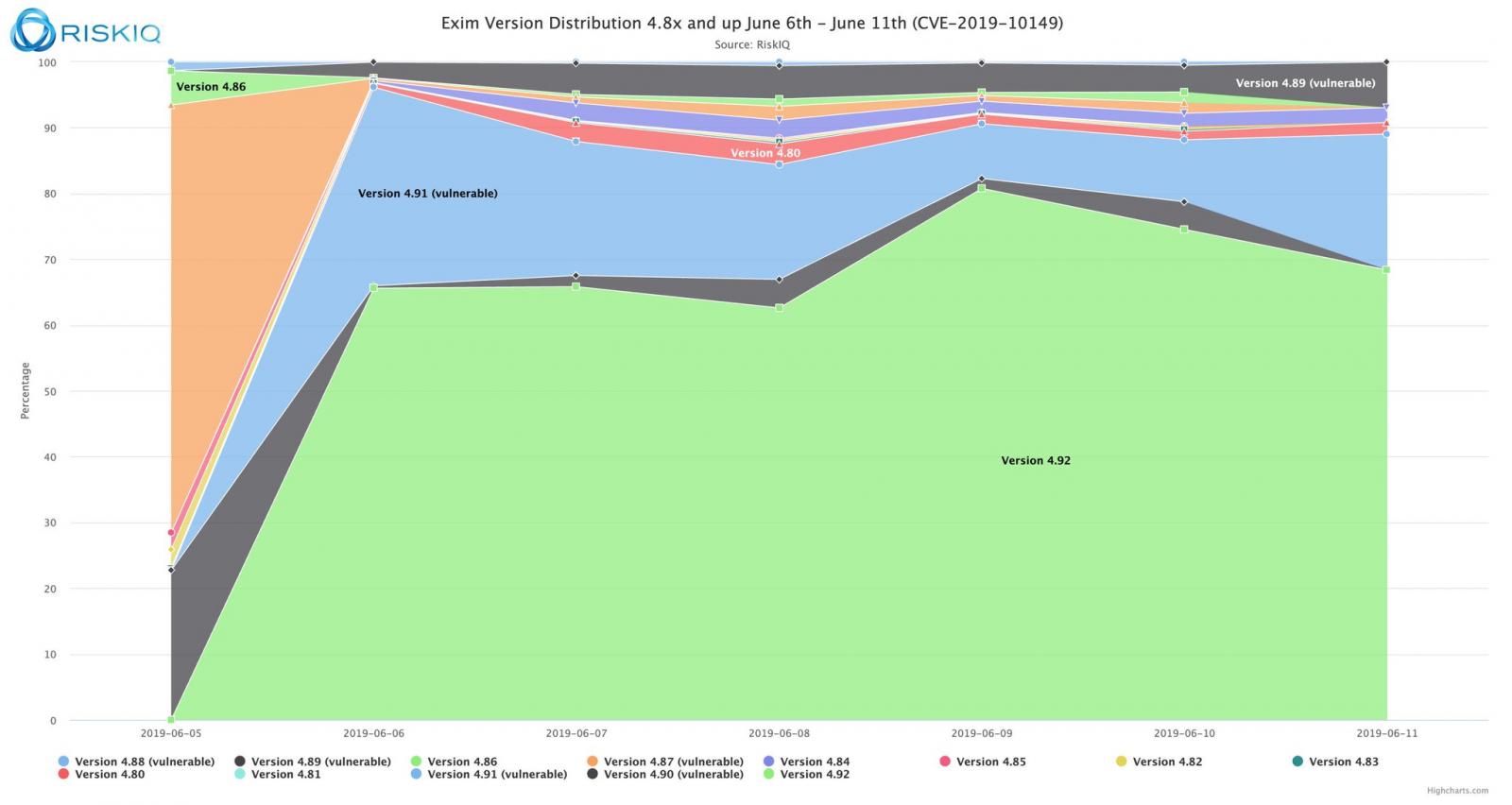
As an update timeline graph shared by Klijnsma shows, almost 70% of all Exim mail servers are currently running version 4.92, the one not vulnerable to these ongoing attacks.
To make sure that their machines are not also exploited, all other Exim server admins should follow suit immediately and install the patched 4.92 version.
Payload hosted on the Tor network
Malicious actors are actively exploiting all vulnerable mail servers they can find by using a Bash script uploaded to "from a tor hidden service (an7kmd2wp4xo7hpr) via tor2web 'routing' services" after exploiting the Exim flaw.
The initially deployed script on exploited Exim servers will then download another script designed to check if OpenSSH is installed on the compromised machine.
Subsequently, if OpenSSH is not present, it will install it using the APT (Advanced Package Tool) package manager together with several other tools, and start it to enable root logins via SSH using a private/public RSA key for authentication.
This way, the attackers get root access to all the Exim servers they manage to compromise as explained by Amit Serper, head of security research at Cybereason.
4/4 That means that if your server was exploited, the attackers have root access to your server via private/public key authentication. I'll start working on a blog post about this in the @cybereason nocturnus blog. Watch my twitter account for details. pic.twitter.com/TvSDVvRn4v
— Amit Serper (@0xAmit) June 13, 2019
Second stream of attacks targeting Exim servers
More attacks have been launched using a not-so-well "camouflaged" server as discovered by Freddie Leeman on June 9, with the hackers dropping the script used to exploit vulnerable Exim servers from 173[.]212[.]214[.]137/s, as initially reported by ZDNet.
"Just detected the first attempts to exploit recent Exim remote command execution (RCE) security flaw (CVE-2019-10149)," said Leeman.
Just as in the case of the previously described attacks launched from a Tor network server, this one will also use the initially dropped script will download a second one that deploys multiple binary payload variants onto the compromised machines.
Leeman stated that he "detected multiple variants and they are changing the scripts too. The latest versions are directly downloading the binary payload and running it, skipping the gathering of system data and posting it."
Just detected the first attempts to exploit recent #exim remote command execution (RCE) security flaw (CVE-2019-10149). Tries to downloads a script located at http://173.212.214.137/s (careful). If you run Exim, make sure it's up-to-date. @qualys pic.twitter.com/s7veGBcKWO
— Freddie Leeman (@freddieleeman) June 9, 2019
Update: Added an Exim update timeline provided by RiskIQ's Yonathan Klijnsma.
Top 10 MITRE ATT&CK© Techniques Behind 93% of Attacks
Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.











Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now